What is a proxy and how to choose for your task
23 Sep 2025
Reading time ~ 13 mins
A proxy server is an intermediary between your device and your site. It sends a request instead of you and returns a response, substituting its IP address. As a result, you gain access to the content you want, reduce the risk of blocking, and you can work with multiple accounts safer.
- when it’s useful. Access to regional content, work with ads and social networks, parsing, automation, additional privacy in the browser and applications.
- what to choose for specific tasks. For maximum speed and cost savings, data centers are suitable; when the “human” trace is important and the tolerance of the sites is higher – residency or mobile; For a stable static address – ISP.
- According to the protocols. HTTP/HTTPS is convenient for web tasks and parsers, SOCKS5 is universal for applications and messengers.
- IP version. IPv4 is compatible everywhere; IPv6 gives large pools and favorable cost if the services support it.
- How to start. Determine the goals, select the type for your script, connect in the browser or the desired program, check the IP on the check. ready to try – look proxy tariffs.
What is proxy in simple words
A proxy is an intermediate server that receives your request to the site, sends it on its own behalf and returns a response. For the target resource, you look like a user with a proxy IP address. This helps to change geolocation, distribute the load during automation and carefully separate the work sessions.
It is important to understand how proxies differ from other technologies. NAT on the router simply ‘throws’ your connections and does not change the external IP – sites still see the address of your provider. The VPN creates an encrypted tunnel and changes the route of all device traffic to one output IP. Proxies work pointwise: you set up a specific browser, parser or bot and gain control – you can run several independent sessions, manage address pool and rotation.
How it looks in practice: the application sends the request not directly, but to the proxy (host: port with login / password or through the list of allowed IPs). The proxy establishes a connection to the site and passes the response back. Web tasks often use HTTP/HTTPS (including a tunnel through Connect), for applications – universal SOCKS5. If the site is running on HTTPS, the content is transmitted encrypted between you and the site; The proxy sees only the facts of the connections, not the form data.
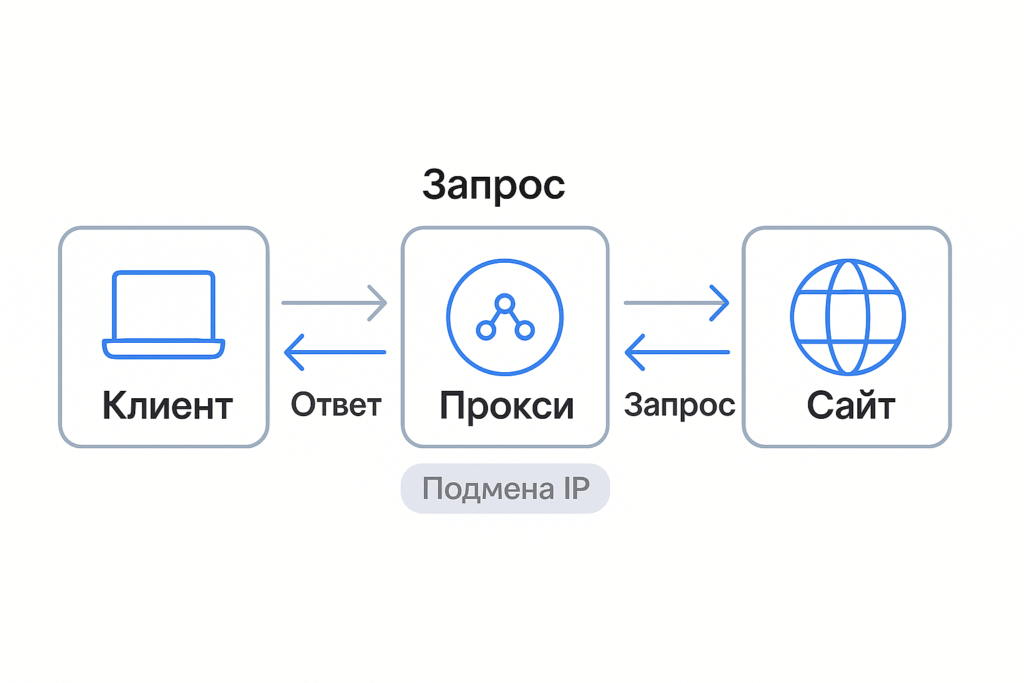
How does a proxy work?
The easiest way is to imagine a proxy as a ‘transfer’ between the application and the site.
- The application sends a request not to the site, but to the proxy address (host:port).
- The proxy establishes a connection to the target resource and forwards your request on its own behalf.
- The answer comes to the proxy and returns to the application. For the site you are the IP address of the proxy.
protocols in a nutshell
- HTTP/HTTPS proxy. work with web requests. For protected sites, the Connect method is used, which creates a tunnel to the destination host. HTTPS content remains encrypted between you and the site – the proxy sees only the connection and metadata (address, time, volume).
- Socks5. Universal option at the TCP/UDP level. Suitable not only for the browser, but also for applications, messengers, parsers and bots. It does not interfere with the protocols of the application and therefore is more flexible in extraordinary cases.
Authorization and access
- Login / Password – specified in the settings.
- IP List – Access is only allowed from your addresses.
- Mass tasks often use address pools and IP rotation at a given interval.
What affects quality
- Delay (ping) – affects responsiveness.
- Bandwidth is important for downloading media and speed parsing.
- Stability (uptime) and timeouts determine how often sessions are interrupted.
- Anonymity is the correct work with headers and the absence of DNS/WeBRTC/IPv6 leaks.
Bottom line: the proxy does not “break” encryption and does not change the work of your programs – it only adds an intermediate node with the desired IP and access rules. It is due to this that you can fine-tune scenarios, separate sessions and scale connections without unnecessary risks.
where proxies really help
Multi-accounting and SMM. When platforms strictly monitor behavior, it is important to separate sessions, countries, and browser fingerprints. For a “human” profile and a smaller number of captchas, they take the addresses of home providers – the format is suitable Resident Proxies. If the anti-fraud is especially strict, the dynamic rotation of IP in mobile operators helps – Mobile Resident Proxies.
Parsing and automation. A large volume of requests requires a pool of addresses, limits and rotation. For better speed and price ratio, data center solutions are more often chosen; With sensitive resources, part of the traffic is transferred to ‘human’ IP. On constant flows, tariffs are more profitable without traffic restrictions – look Unlimited Resident Proxies.
Checking geo-receipt and local prices. Marketers and product teams test how the site looks to different countries and cities, compare prices and availability. Here the necessary geos, stable sessions and rotation control are important.
Access to regional content and SaaS. If the service is closed to your region or shows a different directory, the proxy helps you ‘remain’ in the desired country without restructuring the entire device’s network configuration.
Teamwork and traffic control. The local proxy in the office simplifies website permissions, saves traffic with caching and sets uniform security rules.
The task of choice for tasks is simple: speed and price – data center; maximum trust – resident; Complex sites and frequent rotation are mobile. In the next section, we will analyze the types in more detail and show where which option is appropriate.
Proxy types
Proxy types differ in purpose, origin, protocol, anonymity level and IP version.
by appointment
- Forward Proxy is a classic intermediary for the client: the application gains access to the Internet through a proxy.
- Reverse proxy – stands in front of the site and distributes incoming traffic, caches, protects (not for user anonymity).
by origin/placement
- Data center (DC). Maximum speed and predictability, optimal for parsing and inexpensive scale tasks.
- Resident. IP home providers: natural behavior for sites, higher multi-accounting tolerance. Check out our article about Resident Proxies.
- Mobile. 3G/4G/5G operator addresses with frequent rotation: the best choice for demanding platforms.
- ISP proxy. Dedicated static IP from the ISP: a compromise between price, stability and trust.
According to the protocol
- HTTP/HTTPS. convenient for web tasks and parsers; Support Connect tunneling for HTTPS.
- Socks5. Universal transport at the TCP/UDP level – suitable not only for the browser, but also for applications and bots.
in terms of anonymity
- Transparent transmit the original IP; Anonymous hide it; Elite masks the very fact of using the proxy.
according to IP
- IPv4 – maximum service compatibility.
- IPv6 – huge pools and favorable cost; Choose if the sites you need support it.
Brief memo of choice
| Type | where appropriate | Pros | Confines |
| Data Center (DC) | Parsing, load testing, mass tasks | speed, price, predictability | easier to detect on strict sites |
| Residents | SMM, multi-accounting, sensitive services | Natural traffic, higher tolerance | more expensive than data centers |
| Mobile | The most demanding platforms, frequent rotation | High Trust, Dynamic IP | Rotation/speed dependence |
| ISP proxy | Static trusted IP, long sessions | Stability, price/trust balance | pools are smaller than those of data-center |
| IPv6 Resident | Scaling by country/subnets | large pools, favorable cost | Need IPv6 support on target sites |
Proxy vs vpn – what to choose for the task
VPN directs all device traffic through an encrypted tunnel to one output node. This is convenient for general privacy, work from public networks and access to services closed to your region. Cons – a single ‘funnel’ for all applications, it is more difficult to parallelize different countries and IPs, higher overhead costs.
Proxies are configured point-wise for a specific browser, bot, or parser. You can run dozens of independent sessions, manage address pools and rotation, select a country for each task. Overhead costs are lower and scaling is easier. Encryption depends on the protocol and site: with HTTPS content is already encrypted between the client and the resource.
when something is appropriate
- Daily privacy, public Wi-Fi, corporate access → More convenient VPN.
- Multi-accounting, SMM, parsing, A/B geo-content tests, simultaneous work with different countries → more convenient proxy (flexible rotation and individual IPs for each session).
- Long stable sessions with a ‘human’ profile → proxy with provider addresses (resident/mobile/isp).
- Maximum speed on volumes → Data center solutions.

Is it possible to combine
yes. A frequent scenario is the VPN as an external “case” for the network, and inside the application is a proxy for managing IP and GEO. Important:
- check DNS and WebRTC for leaks;
- understand the exit chain (so as not to get an unexpected region);
- Do not mix too aggressive rotation with ‘long’ sessions.
How to choose Safe: Checklist
- Provider and reputation. Look how old the market is, if there are legal data, SLAs and real cases.
- networks and ASN. The more diverse the subnets and autonomous systems, the lower the chance of mass bans and captchas.
- Uptime and stability. The norm is ≥99% of uptime, predictable timeouts, without ‘drawn’ during peak hours.
- speed and delay. For parsing and downloading media, bandwidth and ping to target sites are important.
- Anonymity without leaks. Check the headers, DNS/WeBRTC/IPv6 leaks and the HTTPS tunnel is working correctly.
- Rotation and pools. You need managed intervals, static/dynamic IP to choose from, the ability to issue “1 account = 1 IP”.
- Geography. Available countries/cities, pool depth in the right regions, quickly adding new locations.
- Access and security. Choice between login/password and ip-whitelist, CIDR restriction, connection logs.
- support and integration. Answers 24/7, documentation, ready-made instructions for browsers, parsers and bots, if necessary – API.
- Rates and test. Trial access/return guarantee, fair quotas for traffic and sessions.
Configure and check proxy: short instruction
- Get access. Write down the host, port, and authorization method – login/password or adding your IP to the whitelist. If you have a dynamic IP at home, login/password authorization is preferable.
- Set up in your browser or app.
- Browser: Specify HTTP/HTTPS or SOCKS5 proxy in system/network settings. For HTTPS, turn on tunneling (usually this is done automatically via Connect).
- parser/bot: add host:port and authorization; If necessary, select Sticky sessions or rotation.
- Check that IP and geo are correct. Open any IP checker, make sure in the country/city and the desired IP version (IPv4/IPv6). Check ASN if the ‘human’ origin of the address is important.
- Avoid leaks. Check DNS/WeBRTC/IPv6. If necessary, disable WebRTC in the browser or enable ‘proxy DNS’ for SOCKS5 so that name requests do not bypass.
- Check through the proxy checker. Measure ping, stability, download speed. Check if there are frequent timeouts and breaks in long sessions.
- Debug the rotation policy and limits.
- For multi-accounting, use the 1 account = 1 IP rule or small groups of accounts per IP.
- For parsing, set the frequency of requests, pauses and backups so as not to catch 429/captcha.
- For long sessions – static/sticky sessions without aggressive rotation.
Typical errors: incorrect protocol (socks instead of HTTP and vice versa), the wrong port, IP is not added to WhiteList, VPN + proxy mixing with an unexpected region change, DNS leaks, IPv6 enabled, when the target service does not support it.
Frequent questions about proxy
- Do proxies encrypt traffic?
Not on their own. HTTP proxy is not encrypted, and with HTTPS, data is encrypted between you and the TLS site. SOCKS5 is a transport layer without encryption. You need an ‘through’ encrypted channel – use sites via HTTPS or combine with VPN. - Why does the site recognize a proxy and ask for a captcha/block?
The reasons are behavioral patterns (frequency, parallelism), known subnets and ASNs, inconsistent headings, DNS/WeBRTC/IPv6 leaks, Cook/fingerprint traces. Natural IPs (Resident/Mobile/ISP), Request Limits, Account Warming, Correct Headers and Disable Leaks help. - How much IP do you need for multi-accounting?
Secure rule is ‘1 account = 1 IP’. Sometimes small groups (2–3 IP accounts) with different sessions and fingerprints are allowed. For long sessions, select static or sticky addresses. - Is it possible to use VPN and proxy at the same time?
Yes: VPN is an external encrypted tunnel, a proxy control IP and GEO for a particular program. Check what DNS requests go through, and do not mix aggressive rotation with long sessions. - What is the difference between ISP proxies and data centers?
ISPs are static addresses for real providers: higher site trust and long session stability than data centers at a more moderate price than “pure” resident. - When exactly do you get mobile proxies?
When the anti-fraud is strict (social networks, marketplaces), frequent rotation and the “human” profile of operator traffic are important. Cons – speed and predictability is lower than that of data center / ISP. - IPv4 or IPv6 – what to choose?
IPv4 – maximum compatibility. IPv6 – huge pools and a favorable price if the target services support it. For large-scale tasks, it is reasonable to combine: the main thread is IPv6, the sensitive points are IPv4. - Sticky vs Rotating – what’s the difference?
Sticky holds the same IP for a given period (suitable for personal accounts, payments, moderation). Rotating changes the address for each request/interval (for parsing and load distribution). Use what matches the scenario and the policy of the site.
which proxy to choose: short conclusion
Proxy is a tool for the task. If speed and price are important, start with data center. You need a “human” profile and higher tolerance of sites – take residence. For the most strict services and frequent rotation, mobile ones are suitable. You need a static, reliable address for long sessions – choose ISP. To scale by country and large pools, it’s reasonable to add IPv6 where it’s supported.
The best way is to test a small pool for your scripts (multiaccounting, parsing, geo-check), set rotation and limits, check leaks and only then scale.
Ready to choose a configuration and plan? Let’s help you pick up the gaps Under your scenarios and choose the best payment model.
Would you like a customized quote?
If you need technical advice or have a specific enquiry, please contact us.
